Kubernetes 认证授权
所有 Kubernetes 集群都有两类用户:由 Kubernetes 管理的服务账号和普通用户。任何客户端访问之前,经由 kubernetes 时,需经过:认证(token, ssl)、授权检查(RBAC)、准入控制(其他资源关联)。
1.1 身份认证
Kubernetes 通过身份认证插件利用客户端证书、持有者令牌(Bearer Token)或身份认证代理(Proxy) 来认证 API 请求的身份。客户端请求(HTTP)发给 APIServer 时,插件会将以下属性关联到请求本身:
用户名:用来辩识最终用户的字符串。
用户 ID:用来辩识最终用户的字符串,旨在比用户名有更好的一致性和唯一性。
用户组:取值为一组字符串,其中各个字符串用来标明用户是某个命名的用户逻辑集合的成员。
附加字段:一组额外的键-值映射,键是字符串,值是一组字符串;用来保存一些鉴权组件可能觉得有用的额外信息。
Tips:
用户经过任何一个认证插件认证通过之后,即表示认证完成,不需再经其他认证插件进行认证。
APIServer 是整个访问请求进入的网关接口,认证用于实现身份识别、授权用于实现权限检查。
1.2 资源类型
客户端通过 RESTful API 风格请求某个特定 API 资源对象 / 集合(列表)时,需要特定标识(Request path)来区分 API 资源类别, 例如:
qingyun@master:~$ kubectl proxy --port=9090
Starting to serve on 127.0.0.1:9090
# Request path: /apis/apps/v1/namespaces/default/deployments/my-deploy/
# 核心群组
qingyun@master:~$ curl http://127.0.0.1:9090/api/v1/namespaces
# 非核心群组
qingyun@master:~$ curl http://127.0.0.1:9090/apis/apps/v1/namespaces/kube-system/deployments/
qingyun@master:~$ curl http://127.0.0.1:9090/apis/apps/v1/namespaces/kube-system/deployments/coredns
资源类型的操作类别:
HTTP request verb(请求动作): get, put, post, delete
API request verb(请求动作): get, list, create, delete, update, patch, watch, proxy
1.3 Account
在 Kubernetes 上,有哪些客户端需要和 APIServer 交互:
集群外部客户端
通过 User Account(用户账号)来访问 APIServer
集群内部客户端(Pod)
通过 Service Account(服务账号)来访问 APIServer
1.3.1 User Account
User account 是在集群外部访问 apiserver 时使用的用户,比如 kubectl 命令就是作为 kubernetes-admin 用户来执行的,其中 ~/.kube/config 指定了用户的证书,以便和 apiserver 互相认证。当然对于 user account 来说,是有多种认证方式的,,但是默认使能是 x509 客户端证书方式。
管理kubectl配置文件:
qingyun@master:~$ kubectl config -h
......
Available Commands:
current-context # 显示当前上下文
delete-cluster # 从kubeconfig中删除指定集群
delete-context # 从kubeconfig中删除指定上下文
delete-user # 从kubeconfig中删除指定用户
get-clusters # 显示kubeconfig中定义的集群
get-contexts # 显示kubeconfig中定义的上下文
get-users # 显示kubeconfig中定义的用户
rename-context # 从kubeconfig中重命名上下文
set # 在kubeconfig文件中设置单个值
set-cluster # 在kubeconfig文件中设置集群
set-context # 在kubeconfig文件中设置上下文
set-credentials # 在kubeconfig文件中设置用户
unset # 在kubeconfig文件中取消设置单个值
use-context # 在kubeconfig文件中设置当前上下文
view # 显示kubeconfig文件信息
......
配置文件详解:
"print config file"
qingyun@master:~$ kubectl config view
apiVersion: v1
clusters: # 集群列表
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.16.104.21:6443
name: kubernetes
contexts: # 上下文列表
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes # 当前上下文: 定义当前那个用户使用那个集群
kind: Config
preferences: {}
users: # 用户列表
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
定义 User account 时我们要附带该账号专门用于到服务器的认证信息。而使用 kubeadm 创建的集群会在初始化过程中自动创建私有 ca 证书,我们可以用 ca.crt, ca.key 签署一个自己自定义的证书和私钥,只要是 APIServer 信任的 ca 签署证书,都可以认证并连入集群。
qingyun@master:~$ ll /etc/kubernetes/pki/
total 84
drwxr-xr-x 3 root root 4096 Aug 29 08:01 ./
drwxr-xr-x 4 root root 4096 Jul 11 08:06 ../
-rw-r--r-- 1 root root 1285 Apr 17 02:15 apiserver.crt
-rw-r--r-- 1 root root 1155 Apr 17 02:15 apiserver-etcd-client.crt
-rw------- 1 root root 1675 Apr 17 02:15 apiserver-etcd-client.key
-rw------- 1 root root 1675 Apr 17 02:15 apiserver.key
-rw-r--r-- 1 root root 1164 Apr 17 02:15 apiserver-kubelet-client.crt
-rw------- 1 root root 1675 Apr 17 02:15 apiserver-kubelet-client.key
-rw-r--r-- 1 root root 1099 Apr 17 02:15 ca.crt
-rw------- 1 root root 1679 Apr 17 02:15 ca.key
-rw-r--r-- 1 root root 41 Aug 29 08:01 ca.srl
drwxr-xr-x 2 root root 4096 Apr 17 02:15 etcd/
-rw-r--r-- 1 root root 1115 Apr 17 02:15 front-proxy-ca.crt
-rw------- 1 root root 1675 Apr 17 02:15 front-proxy-ca.key
-rw-r--r-- 1 root root 1119 Apr 17 02:15 front-proxy-client.crt
-rw------- 1 root root 1675 Apr 17 02:15 front-proxy-client.key
-rwxrwxrwx 1 root root 989 Aug 29 08:01 qingyun.crt*
-rwxrwxrwx 1 root root 887 Aug 29 08:00 qingyun.csr*
-rwxrwxrwx 1 root root 1679 Aug 29 08:00 qingyun.key*
-rw------- 1 root root 1675 Apr 17 02:15 sa.key
-rw------- 1 root root 451 Apr 17 02:15 sa.pub
签署证书(证书持有者必须和用户名保持一致):
"生成证书私钥"
qingyun@master:/etc/kubernetes/pki$ sudo openssl genrsa -out qingyun.key 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
.......................+++++
.................................................+++++
e is 65537 (0x010001)
"证书签署请求"
qingyun@master:/etc/kubernetes/pki$ sudo openssl req -new -key qingyun.key -out qingyun.csr -subj "/CN=qingyun"
"进行证书签署"
qingyun@master:/etc/kubernetes/pki$ sudo openssl x509 -req -in qingyun.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out qingyun.crt -days 365
Signature ok
subject=CN = qingyun
Getting CA Private Key
"查看证书信息"
qingyun@master:/etc/kubernetes/pki$ openssl x509 -in qingyun.crt -text -noout
Certificate:
......
Subject: CN = qingyun
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
......
qingyun@master:/etc/kubernetes/pki$ sudo chmod 777 qingyun.*
新建用户:
"新建用户"
qingyun@master:/etc/kubernetes/pki$ kubectl config set-credentials qingyun --client-certificate=./qingyun.crt --client-key=./qingyun.key --embed-certs=true
User "qingyun" set.
qingyun@master:/etc/kubernetes/pki$ kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.16.104.21:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: qingyun
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
设置上下文:
"设置context"
qingyun@master:/etc/kubernetes/pki$ kubectl config set-context qingyun@kubernetes --cluster=kubernetes --user=qingyun
Context "qingyun@kubernetes" created.
qingyun@master:/etc/kubernetes/pki$ kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.16.104.21:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: qingyun
name: qingyun@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: qingyun
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
"切换context"
qingyun@master:/etc/kubernetes/pki$ kubectl config use-context qingyun@kubernetes
Switched to context "qingyun@kubernetes".
qingyun@master:/etc/kubernetes/pki$ kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.16.104.21:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: qingyun
name: qingyun@kubernetes
current-context: qingyun@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: qingyun
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
"没有权限获取资源"
qingyun@master:/etc/kubernetes/pki$ kubectl get pods
Error from server (Forbidden): pods is forbidden: User "qingyun" cannot list resource "pods" in API group "" in the namespace "default"
设置集群:
"设置集群"
qingyun@master:/etc/kubernetes/pki$ kubectl config set-cluster test-k8s --kubeconfig=/tmp/test/test.conf --server="https://172.16.104.250:6443" --certificate-authority=/tmp/test/ca.crt --embed-certs=true
Cluster "test-k8s" set.
qingyun@master:/etc/kubernetes/pki$ kubectl config view --kubeconfig=/tmp/test/test.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.16.104.250:6443
name: test-k8s
contexts: null
current-context: ""
kind: Config
preferences: {}
users: null
1.3.2 Service Account
Service account 是为了方便 Pod 里面的进程调用 Kubernetes API 或其他外部服务而设计的。它与 User account 不同:
User account 是为人设计的,而 service account 则是为 Pod 中的进程调用 Kubernetes API 而设计;
User account 是跨 namespace 的,而 service account 则是仅局限它所在的 namespace;
每个 namespace 都会自动创建一个 default service account
Token controller 检测 service account 的创建,并为它们创建
开启 ServiceAccount Admission Controller 后:
每个 Pod 在创建后都会自动设置 spec.serviceAccount 为 default(除非指定了其他 ServiceAccout)
验证 Pod 引用的 service account 已经存在,否则拒绝创建
如果 Pod 没有指定 ImagePullSecrets,则把 service account 的 ImagePullSecrets 加到 Pod 中
每个 container 启动后都会挂载该 service account 的 token 和 ca.crt 到 /var/run/secrets/kubernetes.io/serviceaccount/
Pod 如何访问 APIServer?
"APIServer服务"
qingyun@master:~$kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 46d
qingyun@master:~$ kubectl describe svc kubernetes
Name: kubernetes
Namespace: default
Labels: component=apiserver
provider=kubernetes
Annotations: <none>
Selector: <none>
Type: ClusterIP
IP Family Policy: SingleStack
IP Families: IPv4
IP: 10.96.0.1
IPs: 10.96.0.1
Port: https 443/TCP
TargetPort: 6443/TCP
Endpoints: 172.16.104.21:6443
Session Affinity: None
Events: <none>
Pod 访问 APIServer 如何认证?
"run app"
qingyun@master:~$ kubectl run myapp --image=zhangyyhub/myapp:v1.0 -n qingyun
pod/myapp created
qingyun@master:~$ kubectl get pods -n qingyun | grep myapp
myapp 1/1 Running 0 13s
"Pod默认使用default service account"
qingyun@master:~$ kubectl get pod myapp -n qingyun -o yaml | grep "serviceAccount"
serviceAccount: default
serviceAccountName: default
- serviceAccountToken:
"查看service account"
qingyun@master:~$ kubectl get sa -n qingyun
NAME SECRETS AGE
default 1 140d
"查看service account详细信息"
qingyun@master:~$ kubectl describe sa default -n qingyun
Name: default
Namespace: qingyun
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: default-token-jsz2q # 使用default-token
Tokens: default-token-jsz2q
Events: <none>
"查看secret"
qingyun@master:~$ kubectl get secret -n qingyun
NAME TYPE DATA AGE
default-token-jsz2q kubernetes.io/service-account-token 3 140d
default service account 仅有获取当前 Pod 自身权限的属性,如何扩展 Pod 的权限?手动创建 service account 并使用该 service account。
如何创建 service account?
"create service account"
qingyun@master:~$ kubectl create serviceaccount mysa --dry-run=client -n qingyun
serviceaccount/mysa created (dry run)
qingyun@master:~$ kubectl create serviceaccount mysa --dry-run=client -n qingyun -o yaml
apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: null
name: mysa
namespace: qingyun
qingyun@master:~$ kubectl create serviceaccount adminsa -n qingyun
serviceaccount/adminsa created
"get service account"
qingyun@master:~$ kubectl get sa -n qingyun
NAME SECRETS AGE
adminsa 1 13s
default 1 133d
qingyun@master:~$ kubectl describe sa adminsa -n qingyun
Name: adminsa
Namespace: qingyun
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: adminsa-token-mtcwj # 系统自动为service account生成secret信息(sa连接k8s系统的认证信息)
Tokens: adminsa-token-mtcwj
Events: <none>
qingyun@master:~$ kubectl get secret -n qingyun
NAME TYPE DATA AGE
adminsa-token-mtcwj kubernetes.io/service-account-token 3 63s
default-token-jsz2q kubernetes.io/service-account-token 3 133d
ixtep-tls kubernetes.io/tls 2 130d
mysql-root-password Opaque 1 37d
tomcat-secret kubernetes.io/tls 2 42d
Pod 如何使用 service account?
apiVersion: v1
kind: Pod
metadata:
name: demo-sa-pod
namespace: qingyun
# labels: {app: demo-app, tier: frontend}
labels:
app: demo-app
tier: frontend
spec:
containers:
- name: demo-container
image: zhangyyhub/myapp:v1.0
ports:
- name: http
containerPort: 80
serviceAccountName: adminsa
Tips:
Secret 可以在定义 Pod 时使用 pod.spec.imagePullSecrets 字段引用 secret,当然该方法有一些缺陷(泄漏信息)。我们也可以使用 pod.spec.serviceAccountName 定义 service account,而 serivce account 可以附带认证到私有仓库的认证信息的。
qingyun@master:~$ kubectl get sa -n qingyun
NAME SECRETS AGE
adminsa 1 7d2h
default 1 140d
qingyun@master:~$ kubectl describe sa adminsa -n qingyun
Name: adminsa
Namespace: qingyun
Labels: <none>
Annotations: <none>
Image pull secrets: <none> # 定义secret
Mountable secrets: adminsa-token-mtcwj
Tokens: adminsa-token-mtcwj
Events: <none>
2、授权
Kubernetes 使用 API 服务器对 API 请求进行鉴权。它根据所有策略评估所有请求属性来决定允许或拒绝请求。一个 API 请求的所有部分都必须被某些策略允许才能继续。这意味着默认情况下拒绝权限。
当系统配置了多个鉴权模块时,Kubernetes 将按顺序使用每个模块。如果任何鉴权模块批准或拒绝请求,则立即返回该决定,并且不会与其他鉴权模块协商。如果所有模块对请求没有意见,则拒绝该请求。 被拒绝响应返回 HTTP 状态代码 403。
授权模块:
Node
v1.7+ 支持 Node 授权,配合 NodeRestriction 准入控制来限制 kubelet 仅可访问 node、endpoint、pod、service 以及 secret、configmap、PV 和 PVC 等相关的资源。
ABAC
基于属性的访问控制(ABAC)定义了访问控制范例,通过将属性组合在一起的策略来授予用户访问权限。
RBAC
在 Kubernetes1.6 版本中新增角色访问控制机制(Role-Based Access,RBAC)让集群管理员可以针对特定使用者或服务账号的角色,进行更精确的资源访问控制。
Webhook
WebHook 是一个自定义 HTTP 回调方法:事件发生时发送 HTTP POST,通过 HTTP POST 进行简单的事件通知。实现 WebHooks 的 Web 应用程序将在某些事件发生时向URL发送消息。
Custom Modules
可以创建 Kubernetes 的(Custom Modules)自定义模块。
目前主要以 RBAC(Role-Based Access)基于角色的访问控制来进行授权。
2.1 授权逻辑
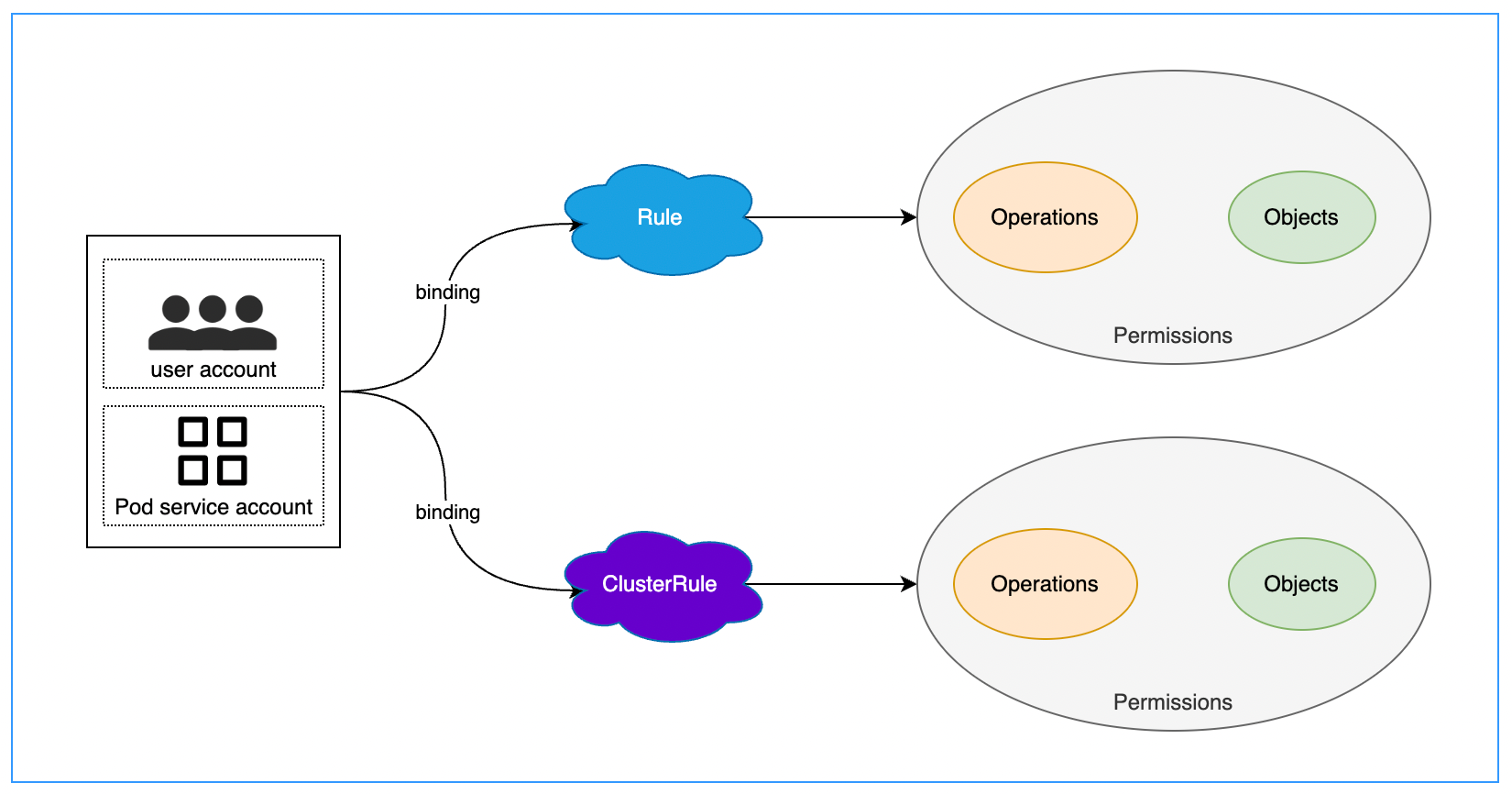
Role(get, list...)
role
clusterrole
Account
user account
service account
Binding
rolebinding
clusterrolebinding
Role 是一组权限(Permissions)的集合,定义相关策略规则(Operations---Objects)的信息,基于 Binding 绑定 Account,使 Account 扮演该 Role(角色),进而拥有该 Role(角色)的访问控制权限。
Role 是名称空间级别资源,ClusterRole 为集群级别资源。
Rolebinding binding Role(namespace level permissions)
ClusterRolebinding binding ClusterRole(cluster level permissions)
Rolebinding binding ClusterRole(namespace level permissions)
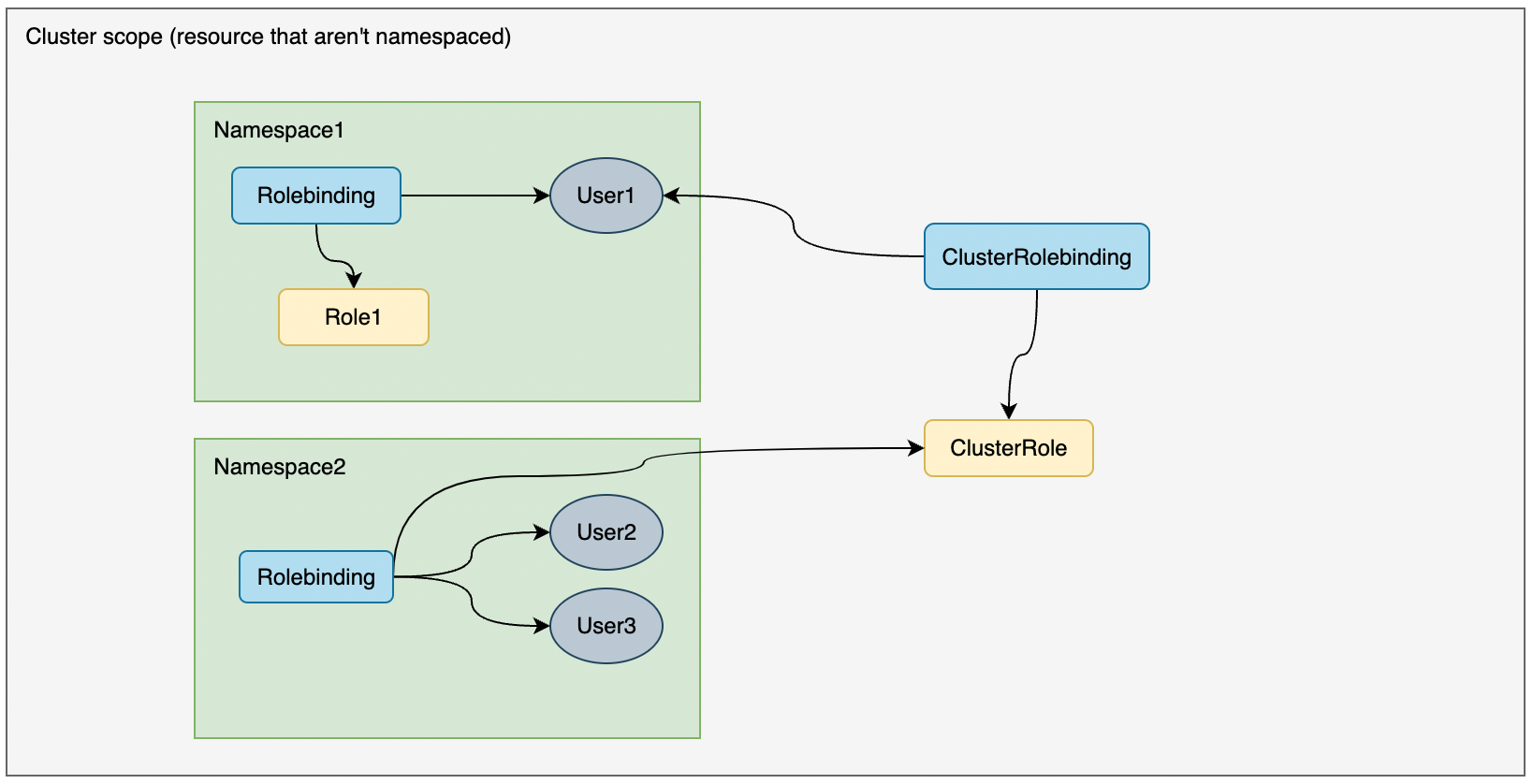
2.2 授权示例
Rolebinding binding Role:
"create role"
qingyun@master:~$ kubectl create role pods-reader --verb=get,list,watch --resource=pods --dry-run=client -n qingyun -o yaml > role-demo.yaml
qingyun@master:~$ cat role-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: pods-reader
namespace: qingyun
rules:
- apiGroups: # 对哪些api群组内的资源做操作
- ""
resources:
- pods
verbs:
- get
- list
- watch
qingyun@master:~$ kubectl apply -f role-demo.yaml
role.rbac.authorization.k8s.io/pods-reader created
"get role"
qingyun@master:~$ kubectl get role -n qingyun
NAME CREATED AT
pods-reader 2022-09-10T12:55:57Z
qingyun@master:~$ kubectl describe role pods-reader -n qingyun
Name: pods-reader
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
pods [] [] [get list watch]
"create rolebinding"
qingyun@master:~$ kubectl create rolebinding qingyun-read-pods --role=pods-reader --user=qingyun -n qingyun
rolebinding.rbac.authorization.k8s.io/qingyun-read-pods created
"get rolebinding"
qingyun@master:~$ kubectl get rolebinding -n qingyun
NAME ROLE AGE
qingyun-read-pods Role/pods-reader 11s
qingyun@master:~$ kubectl describe rolebinding qingyun-read-pods -n qingyun
Name: qingyun-read-pods
Labels: <none>
Annotations: <none>
Role:
Kind: Role
Name: pods-reader
Subjects:
Kind Name Namespace
---- ---- ---------
User qingyun
"set current context: qingyun@kubernetes"
qingyun@master:~$ kubectl config use-context qingyun@kubernetes
Switched to context "qingyun@kubernetes".
"verify"
qingyun@master:~$ kubectl get pods
Error from server (Forbidden): pods is forbidden: User "qingyun" cannot list resource "pods" in API group "" in the namespace "default"
qingyun@master:~$ kubectl get pods -n qingyun
NAME READY STATUS RESTARTS AGE
demo-sa-pod 1/1 Running 0 13d
myapp 1/1 Running 0 6d6h
ClusterRolebinding binding ClusterRole:
"set current context: kubernetes-admin@kubernetes"
qingyun@master:~$ kubectl config use-context kubernetes-admin@kubernetes
Switched to context "kubernetes-admin@kubernetes".
"create clusterrole"
qingyun@master:~/k8sData/deploy/demo/rbac$ kubectl create clusterrole cluster-reader --verb=get,list,watch --resource=pods -o yaml --dry-run=client
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
creationTimestamp: null
name: cluster-reader
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
qingyun@master:~$ kubectl create clusterrole cluster-reader --verb=get,list,watch --resource=pods -o yaml --dry-run=client > clusterrole-demo.yaml
qingyun@master:~$ vim clusterrole-demo.yaml
qingyun@master:~$ cat clusterrole-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cluster-reader
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
qingyun@master:~$ kubectl apply -f clusterrole-demo.yaml
clusterrole.rbac.authorization.k8s.io/cluster-reader created
"delete rolebinding"
qingyun@master:~$ kubectl get rolebinding -n qingyun
NAME ROLE AGE
qingyun-read-pods Role/pods-reader 16h
qingyun@master:~$ kubectl delete rolebinding qingyun-read-pods -n qingyun
rolebinding.rbac.authorization.k8s.io "qingyun-read-pods" deleted
"create clusterrolebinding"
qingyun@master:~$ kubectl create clusterrolebinding qingyun-admin-all-pods --clusterrole=cluster-reader --user=qingyun --dry-run=client -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
creationTimestamp: null
name: qingyun-admin-all-pods
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: qingyun
qingyun@master:~$ kubectl create clusterrolebinding qingyun-admin-all-pods --clusterrole=cluster-reader --user=qingyun --dry-run=client -o yaml > clusterrolebinding-demo.yaml
qingyun@master:~$ vim clusterrolebinding-demo.yaml
qingyun@master:~$ cat clusterrolebinding-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: qingyun-admin-all-pods
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: qingyun
qingyun@master:~$ kubectl apply -f clusterrolebinding-demo.yaml
clusterrolebinding.rbac.authorization.k8s.io/qingyun-admin-all-pods created
"get clusterrolebinding"
qingyun@master:~$ kubectl describe clusterrolebinding qingyun-admin-all-pods
Name: qingyun-admin-all-pods
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: cluster-reader
Subjects:
Kind Name Namespace
---- ---- ---------
User qingyun
"verify: added ik8s users to use qingyun context"
qingyun@master:~$ sudo adduser ik8s
qingyun@master:~$ sudo usermod -G sudo ik8s
qingyun@master:~$ sudo cp -rp ~/.kube/ /home/ik8s/
qingyun@master:~$ sudo chown -R ik8s.ik8s /home/ik8s/
qingyun@master:~$ su - ik8s
Password:
"verify: set current context: qingyun@kubernetes"
ik8s@master:~$ kubectl config use-context qingyun@kubernetes
Switched to context "qingyun@kubernetes".
"verify: get pod"
ik8s@master:~$ kubectl get pods -n qingyun
NAME READY STATUS RESTARTS AGE
demo-sa-pod 1/1 Running 0 13d
myapp 1/1 Running 0 6d22h
ik8s@master:~$ kubectl get pods
NAME READY STATUS RESTARTS AGE
nginx-web 1/1 Running 0 5d23h
nignx-01-5f8b6d99c4-mrl54 1/1 Running 0 4d22h
"verify: cannot be deleted"
ik8s@master:~$ kubectl delete pods nginx-web
Error from server (Forbidden): pods "nginx-web" is forbidden: User "qingyun" cannot delete resource "pods" in API group "" in the namespace "default"
Rolebinding binding ClusterRole:
"delete clusterrolebinding"
qingyun@master:~/k8sData/deploy/demo/rbac$ kubectl delete clusterrolebinding qingyun-admin-all-pods
clusterrolebinding.rbac.authorization.k8s.io "qingyun-admin-all-pods" deleted
"create rolebinding binding clusterrole"
qingyun@master:~/k8sData/deploy/demo/rbac$ kubectl create rolebinding qingyun-read-pods --clusterrole=cluster-reader --user=qingyun -n qingyun --dry-run=client -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: null
name: qingyun-read-pods
namespace: qingyun
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: qingyun
qingyun@master:~/k8sData/deploy/demo/rbac$ kubectl create rolebinding qingyun-read-pods --clusterrole=cluster-reader --user=qingyun -n qingyun --dry-run=client -o yaml > rolebinding-clusterrole-demo.yaml
qingyun@master:~/k8sData/deploy/demo/rbac$ vim rolebinding-clusterrole-demo.yaml
qingyun@master:~/k8sData/deploy/demo/rbac$ cat rolebinding-clusterrole-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: qingyun-read-pods
namespace: qingyun
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: qingyun
qingyun@master:~/k8sData/deploy/demo/rbac$ kubectl apply -f rolebinding-clusterrole-demo.yaml
rolebinding.rbac.authorization.k8s.io/qingyun-read-pods created
"get rolebinding"
qingyun@master:~/k8sData/deploy/demo/rbac$ kubectl describe rolebinding qingyun-read-pods -n qingyun
Name: qingyun-read-pods
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: cluster-reader
Subjects:
Kind Name Namespace
---- ---- ---------
User qingyun
"verify"
qingyun@master:~$ su - ik8s
Password:
ik8s@master:~$ kubectl get pods
Error from server (Forbidden): pods is forbidden: User "qingyun" cannot list resource "pods" in API group "" in the namespace "default"
ik8s@master:~$ kubectl get pods -n qingyun
NAME READY STATUS RESTARTS AGE
demo-sa-pod 1/1 Running 0 13d
myapp 1/1 Running 0 6d22h
2.3 Tips
kubernetes 系统有很多 Role,可以用于学习:
qingyun@master:~$ kubectl get clusterrole
NAME CREATED AT
admin 2022-04-16T18:15:19Z
cluster-admin 2022-04-16T18:15:19Z
......
cluster-admin clusterrole 是 kubernetes 集群默认的管理 Role:
......