kubernetes dashboard
1、背景
Dashboard 是基于网页的 Kubernetes 用户界面。 你可以使用 Dashboard 将容器应用部署到 Kubernetes 集群中,也可以对容器应用排错,还能管理集群资源。你可以使用 Dashboard 获取运行在集群中的应用的概览信息,也可以创建或者修改 Kubernetes 资源 (如 Deployment,Job,DaemonSet 等等)。 例如,你可以对 Deployment 实现弹性伸缩、发起滚动升级、重启 Pod 或者使用向导创建新的应用。
Dashboard 同时展示了 Kubernetes 集群中的资源状态信息和所有报错信息。
官网:https://kubernetes.io/zh-cn/docs/tasks/access-application-cluster/web-ui-dashboard/
2、操作前了解相关配置和要求
了解 Kubernetes 认证授权机制。
3、操作步骤
3.1 部署
"deploy dashboard"
qingyun@master:~$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.5.0/aio/deploy/recommended.yaml
"get pods"
qingyun@master:~$ kubectl get pods -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
dashboard-metrics-scraper-799d786dbf-tph9n 1/1 Running 0 103s
kubernetes-dashboard-546cbc58cd-nvb7z 1/1 Running 0 103s
"get svc"
qingyun@master:~$ kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.110.254.127 <none> 8000/TCP 111s
kubernetes-dashboard ClusterIP 10.101.119.169 <none> 443/TCP 111s
"modification svc type: nodeport"
qingyun@master:~/k8sData/deploy/dashboard$ kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kubernetes-dashboard
service/kubernetes-dashboard patched
"get svc"
qingyun@master:~/k8sData/deploy/dashboard$ kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.110.254.127 <none> 8000/TCP 6m
kubernetes-dashboard NodePort 10.101.119.169 <none> 443:30657/TCP 6m3.2 访问
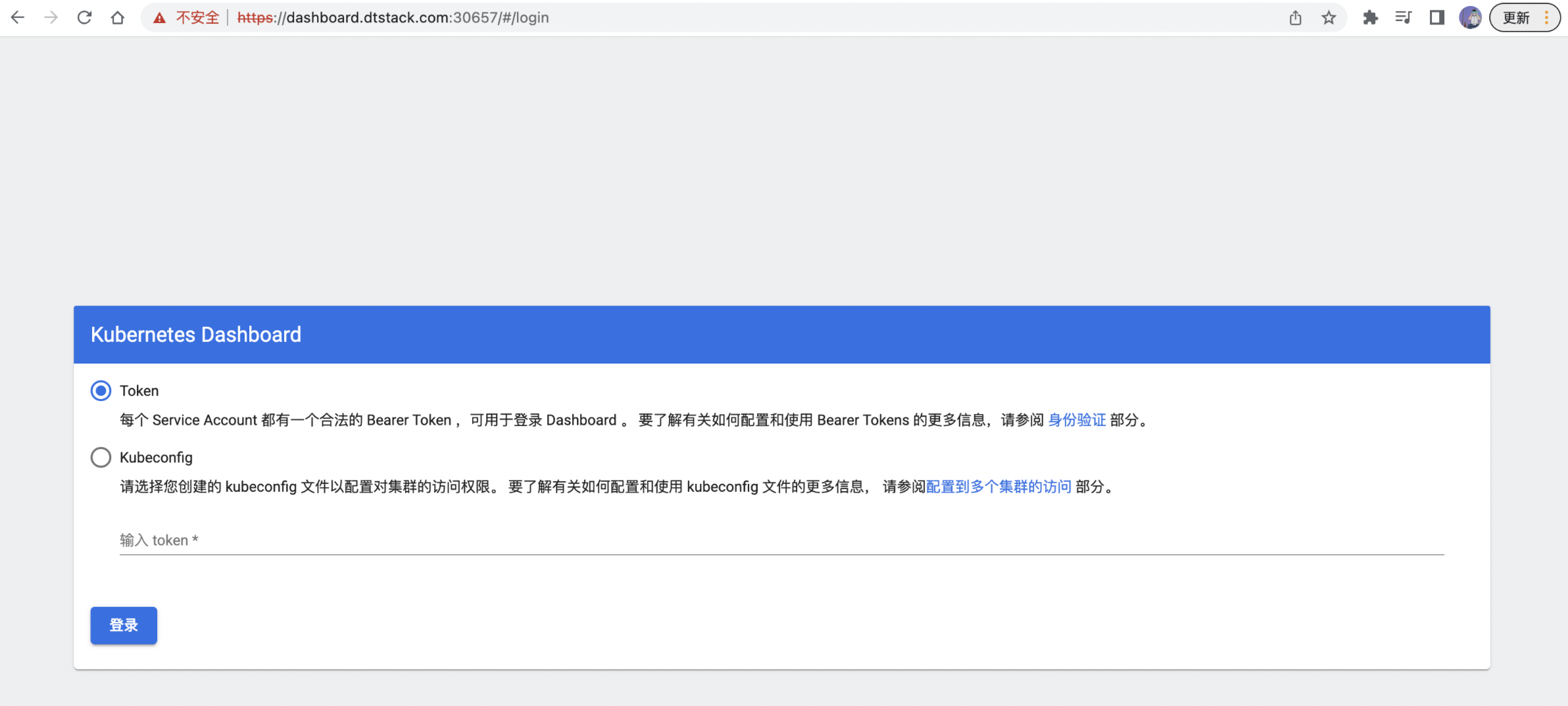
Dashboard 支持 Token, Kubeconfig 认证登陆,需要登陆认证成功才能访问。
由于是通过 Dashboard 管理 Kubernetes 集群资源,所以 Token, Kubeconfig 配置中的 Account 应该为 ServiceAccount。
3.2.1 Token 认证
Clusterrolebinding Binding Clusterrole(cluster-admin):
创建 ServiceAccount,使用 Clusterrolebinding binding Clusterrole(cluster-admin),获取该 ServiceAccount 对应 Secret 中的 Token 信息:
"create serviceaccount" qingyun@master:~$ kubectl create serviceaccount dashboard-admin -n kubernetes-dashboard serviceaccount/dashboard-admin created qingyun@master:~$ kubectl get sa -n kubernetes-dashboard NAME SECRETS AGE dashboard-admin 1 12s default 1 3h25m "create clusterrolebinding" qingyun@master:~$ kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount kubernetes-dashboard:dashboard-admin clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created "get token" qingyun@master:~$ kubectl get secret -n kubernetes-dashboard | grep dashboard-admin dashboard-admin-token-dwgx8 kubernetes.io/service-account-token 3 75m qingyun@master:~$ kubectl describe secret dashboard-admin-token-dwgx8 -n kubernetes-dashboard Name: dashboard-admin-token-dwgx8 Namespace: kubernetes-dashboard Labels: <none> Annotations: kubernetes.io/service-account.name: dashboard-admin kubernetes.io/service-account.uid: 6a7e727a-855a-4d1e-bf3e-3a58af23aed0 Type: kubernetes.io/service-account-token Data ==== namespace: 20 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6Il9BdW1fajFaSEg2MldYQ0UxMFdhWlBkS1UyLXVsNklNTzFuUFNieDlvVm8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tZHdneDgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNmE3ZTcyN2EtODU1YS00ZDFlLWJmM2UtM2E1OGFmMjNhZWQwIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmVybmV0ZXMtZGFzaGJvYXJkOmRhc2hib2FyZC1hZG1pbiJ9.QTmfiv5NYIqxgNFUwZnLSh46a0MP5ftCYeOo3Pmfis9d5s4LoEczg67kB3e7As51wwdmfQO-G8F3-njI8keZFOPrWTmLQfaJ0MbCr6IhGWE4YaG60oi7taQyDeV2q4Aroh4XElHLr9-zUQIB7IBF0EdvrDa-YZdpNADOGcio_YGvNmoCGEXh8PdCvblyAgTLjO0LMFuU0onpR8-p8eiIZJ7qV6AUlW0DAI0W12HdNNi_rLKI88cs8y-Cp0OysEqqn6ghLVUzcUQbXj6tWz-bjBDASDR-kGpo1idXVjxH3SuFRyfI4lsqELILhBI0FyLA04zsEyr-jnSOXLTf0cX6nw ca.crt: 1099 bytes
使用 Token 认证登陆:
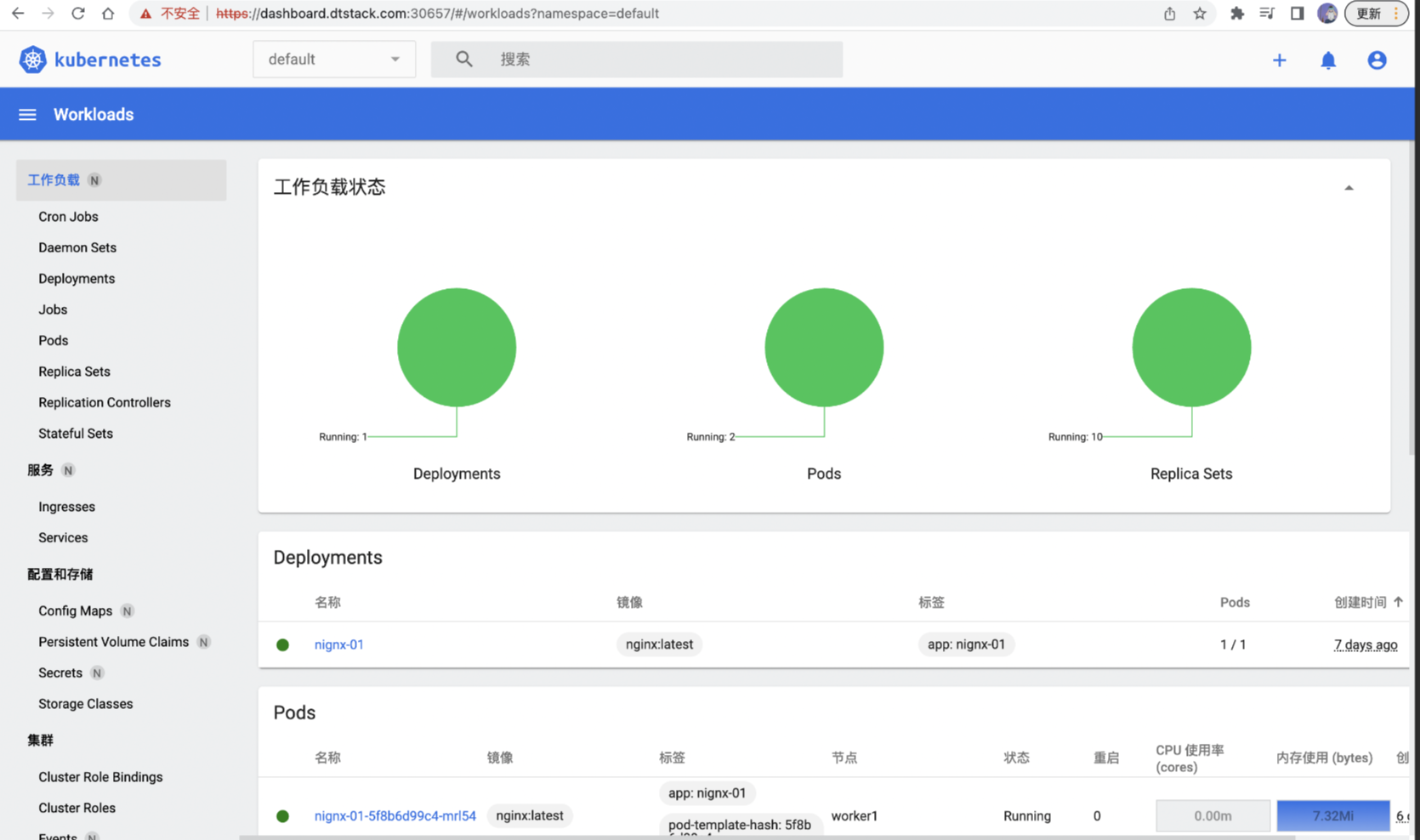
Rolebinding Binding Clusterrole(default-ns-admin):
创建 ServiceAccount,使用 Rolebinding binding Clusterrole(default-ns-admin),获取该 ServiceAccount 对应 Secret 中的 Token 信息:
"create serviceaccount" qingyun@master:~$ kubectl create serviceaccount default-ns-admin -n default serviceaccount/default-ns-admin created "create rolebinding" qingyun@master:~$ kubectl create rolebinding default-ns-admin-rolebinding --clusterrole=admin --serviceaccount=default:default-ns-admin rolebinding.rbac.authorization.k8s.io/default-ns-admin-rolebinding created "get token" qingyun@master:~$ kubectl get secret | grep default-ns-admin default-ns-admin-token-vmx45 kubernetes.io/service-account-token 3 4m22s qingyun@master:~$ kubectl describe secret default-ns-admin-token-vmx45 Name: default-ns-admin-token-vmx45 Namespace: default Labels: <none> Annotations: kubernetes.io/service-account.name: default-ns-admin kubernetes.io/service-account.uid: f39f88fc-84fd-4973-a7fa-869e048ec318 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1099 bytes namespace: 7 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6Il9BdW1fajFaSEg2MldYQ0UxMFdhWlBkS1UyLXVsNklNTzFuUFNieDlvVm8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtbnMtYWRtaW4tdG9rZW4tdm14NDUiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdC1ucy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImYzOWY4OGZjLTg0ZmQtNDk3My1hN2ZhLTg2OWUwNDhlYzMxOCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQtbnMtYWRtaW4ifQ.WydIwYRAYCOEWE0TuBknJU5_WXZKuf3vvoQvNTOdKTG3q3P2yYUhWV9ysoCToQAlpl4ooBDJT1LrKqgju5d_EGgqbVg7vRnq3AUNeiQrowZZCQIXZLwXy1j6TWNRk_wyJDcAyoSEVfrtnp5EhVyEYWqlssPbHxnzmbBNl3pNpQ_SZeMw8-Lr-TSAS5zjTDqZ-M51ccBuyUtVT1bUAxYGs2jx9Ms_EcBJ5vq3TYBIGI2qBG9TQqsDg8lOg8lWKtwJdqaJoyQB8I4SaeyXpEM6cjRKpaqy10eIiB88vO0t4AqjLZQQlETKWlsvIq28dy-rbd5YZsU_CVDpr-UXBueZpg
使用 Token 认证登陆:
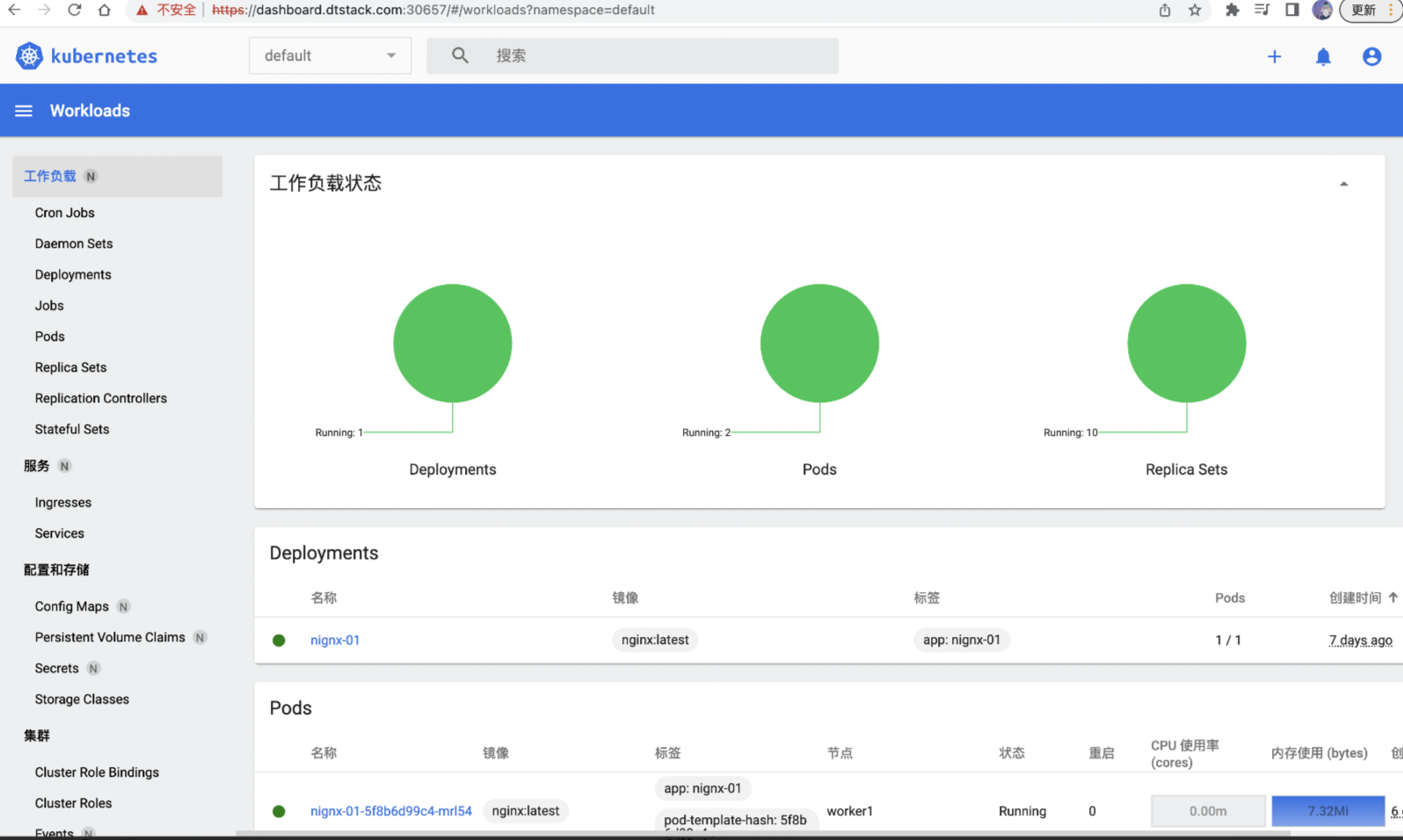
3.2.2 Kubeconfig 认证
set cluster:
"set cluster"
qingyun@master:~$ kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/pki/ca.crt --server="https://172.16.104.21:6443" --embed-certs=true --kubeconfig=/home/qingyun/default-ns-admin.conf
Cluster "kubernetes" set.
"config view"
qingyun@master:~$ kubectl config view --kubeconfig=./default-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.16.104.21:6443
name: kubernetes
contexts: null
current-context: ""
kind: Config
preferences: {}
users: nullset credentials:
"base64解码"
qingyun@master:~$ kubectl get secret | grep default-ns-admin
default-ns-admin-token-vmx45 kubernetes.io/service-account-token 3 29m
qingyun@master:~$ kubectl get secret default-ns-admin-token-vmx45 -o jsonpath={.data.token}
ZXlKaGJHY2lPaUpTVXpJMU5pSXNJbXRwWkNJNklsOUJkVzFmYWpGYVNFZzJNbGRZUTBVeE1GZGhXbEJrUzFVeUxYVnNOa2xOVHpGdVVGTmllRGx2Vm04aWZRLmV5SnBjM01pT2lKcmRXSmxjbTVsZEdWekwzTmxjblpwWTJWaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXVZVzFsYzNCaFkyVWlPaUprWldaaGRXeDBJaXdpYTNWaVpYSnVaWFJsY3k1cGJ5OXpaWEoyYVdObFlXTmpiM1Z1ZEM5elpXTnlaWFF1Ym1GdFpTSTZJbVJsWm1GMWJIUXRibk10WVdSdGFXNHRkRzlyWlc0dGRtMTRORFVpTENKcmRXSmxjbTVsZEdWekxtbHZMM05sY25acFkyVmhZMk52ZFc1MEwzTmxjblpwWTJVdFlXTmpiM1Z1ZEM1dVlXMWxJam9pWkdWbVlYVnNkQzF1Y3kxaFpHMXBiaUlzSW10MVltVnlibVYwWlhNdWFXOHZjMlZ5ZG1salpXRmpZMjkxYm5RdmMyVnlkbWxqWlMxaFkyTnZkVzUwTG5WcFpDSTZJbVl6T1dZNE9HWmpMVGcwWm1RdE5EazNNeTFoTjJaaExUZzJPV1V3TkRobFl6TXhPQ0lzSW5OMVlpSTZJbk41YzNSbGJUcHpaWEoyYVdObFlXTmpiM1Z1ZERwa1pXWmhkV3gwT21SbFptRjFiSFF0Ym5NdFlXUnRhVzRpZlEuV3lkSXdZUkFZQ09FV0UwVHVCa25KVTVfV1haS3VmM3Z2b1F2TlRPZEtURzNxM1AyeVlVaFdWOXlzb0NUb1FBbHBsNG9vQkRKVDFMcktxZ2p1NWRfRUdncWJWZzd2Um5xM0FVTmVpUXJvd1paQ1FJWFpMd1h5MWo2VFdOUmtfd3lKRGNBeW9TRVZmcnRucDVFaFZ5RVlXcWxzc1BiSHhuem1iQk5sM3BOcFFfU1plTXc4LUxyLVRTQVM1empURHFaLU01MWNjQnV5VXRWVDFiVUF4WUdzMmp4OU1zX0VjQko1dnEzVFlCSUdJMnFCRzlUUXFzRGc4bE9nOGxXS3R3SmRxYUpveVFCOEk0U2FleVhwRU02Y2pSS3BhcXkxMGVJaUI4OHZPMHQ0QXFqTFpRUWxFVEtXbHN2SXEyOGR5LXJiZDVZWnNVX0NWRHByLVVYQnVlWnBn
qingyun@master:~$ kubectl get secret default-ns-admin-token-vmx45 -o jsonpath={.data.token} | base64 -d
eyJhbGciOiJSUzI1NiIsImtpZCI6Il9BdW1fajFaSEg2MldYQ0UxMFdhWlBkS1UyLXVsNklNTzFuUFNieDlvVm8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtbnMtYWRtaW4tdG9rZW4tdm14NDUiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdC1ucy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImYzOWY4OGZjLTg0ZmQtNDk3My1hN2ZhLTg2OWUwNDhlYzMxOCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQtbnMtYWRtaW4ifQ.WydIwYRAYCOEWE0TuBknJU5_WXZKuf3vvoQvNTOdKTG3q3P2yYUhWV9ysoCToQAlpl4ooBDJT1LrKqgju5d_EGgqbVg7vRnq3AUNeiQrowZZCQIXZLwXy1j6TWNRk_wyJDcAyoSEVfrtnp5EhVyEYWqlssPbHxnzmbBNl3pNpQ_SZeMw8-Lr-TSAS5zjTDqZ-M51ccBuyUtVT1bUAxYGs2jx9Ms_EcBJ5vq3TYBIGI2qBG9TQqsDg8lOg8lWKtwJdqaJoyQB8I4SaeyXpEM6cjRKpaqy10eIiB88vO0t4AqjLZQQlETKWlsvIq28dy-rbd5YZsU_CVDpr-UXBueZpg
"保存到变量"
qingyun@master:~$ DEFAULT_NS_ADMIN_TOKEN=$(kubectl get secret default-ns-admin-token-vmx45 -o jsonpath={.data.token} | base64 -d)
qingyun@master:~$ echo $DEFAULT_NS_ADMIN_TOKEN
eyJhbGciOiJSUzI1NiIsImtpZCI6Il9BdW1fajFaSEg2MldYQ0UxMFdhWlBkS1UyLXVsNklNTzFuUFNieDlvVm8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtbnMtYWRtaW4tdG9rZW4tdm14NDUiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdC1ucy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImYzOWY4OGZjLTg0ZmQtNDk3My1hN2ZhLTg2OWUwNDhlYzMxOCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQtbnMtYWRtaW4ifQ.WydIwYRAYCOEWE0TuBknJU5_WXZKuf3vvoQvNTOdKTG3q3P2yYUhWV9ysoCToQAlpl4ooBDJT1LrKqgju5d_EGgqbVg7vRnq3AUNeiQrowZZCQIXZLwXy1j6TWNRk_wyJDcAyoSEVfrtnp5EhVyEYWqlssPbHxnzmbBNl3pNpQ_SZeMw8-Lr-TSAS5zjTDqZ-M51ccBuyUtVT1bUAxYGs2jx9Ms_EcBJ5vq3TYBIGI2qBG9TQqsDg8lOg8lWKtwJdqaJoyQB8I4SaeyXpEM6cjRKpaqy10eIiB88vO0t4AqjLZQQlETKWlsvIq28dy-rbd5YZsU_CVDpr-UXBueZpg
"set credentials"
qingyun@master:~$ kubectl config set-credentials default-ns-admin-user --token=$DEFAULT_NS_ADMIN_TOKEN --kubeconfig=/home/qingyun/default-ns-admin.conf
User "default-ns-admin-user" set.
"config view"
qingyun@master:~$ kubectl config view --kubeconfig=/home/qingyun/default-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.16.104.21:6443
name: kubernetes
contexts: null
current-context: ""
kind: Config
preferences: {}
users:
- name: default-ns-admin-user
user:
token: REDACTEDset up and use context:
"set context"
qingyun@master:~$ kubectl config set-context default-ns-admin-user@kubernetes --cluster=kubernetes --user=default-ns-admin-user --kubeconfig=/home/qingyun/default-ns-admin.conf
Context "default-ns-admin-user@kubernetes" created.
"set use context"
qingyun@master:~$ kubectl config use-context default-ns-admin-user@kubernetes --kubeconfig=/home/qingyun/default-ns-admin.conf
Switched to context "default-ns-admin-user@kubernetes".
"config view"
qingyun@master:~$ kubectl config view --kubeconfig=/home/qingyun/default-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.16.104.21:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: default-ns-admin-user
name: default-ns-admin-user@kubernetes
current-context: default-ns-admin-user@kubernetes
kind: Config
preferences: {}
users:
- name: default-ns-admin-user
user:
token: REDACTED此时,我们供 Kubernetes Dashboard 使用的 Kubeconfig 文件就创建完毕了,可使用该文件进行验证登陆。
4、注意事项
注意对 Token, Kubeconfig 所拥有的权限进行检查,保证最小化权限管理准则。
5、结果检查
通过 Kubernetes Dashboard 页面进行集群资源管理。